The one with the open endpoints

What would you do if you found a company was careless with its data? Like.. the personal data of over a million people kind of careless?
You're faced with either reporting them (with unknown consequences to you and them) or letting them sweep it under the rug.
In August 2024, I stumbled upon two open API endpoints of an Australian-wide Sports-team management app, all while just trying to get player stats.
Here's how it all happened.

The plan? Use their back-end to catch when teams are stacking players.
Clubs often have teams in higher and lower leagues, with players moving up or down each week as coaches see fit. Against a difficult team, clubs may stack their team with a few more than the rules allow, but the app makes it time-consuming to catch.
Down to the basement with a black hoodie and 30 Mountain Dews, time to put on some huge headphones and listen to ASMR while we answer:
Given a teamsheet, how many players are from higher divisions?

Question one: Can we even get data?
The mobile app feels more feature-rich than the web app, so an on-device packet sniffer is employed. Encrypted traffic, no good. Strike one. (*1)
Their support chat says no Public API exists. Strike two.
Luckily, requests from the web app only require a bearer token, and show enough promise to do what we want. Bingo!
With the trusty Chrome network tab open, I've now got a directory of all useful API calls. And they all return successfully when requested by a local script. We're in the data business, baby!
Here's where my trust in the world started breaking down

To catch the player, we need to see them on a teamsheet. For a teamsheet, we need an opposition team ID and a match ID:
We look to the /results endpoint, which lists all IDs of completed games. We get over 7000 records here, because the average Joe schmuck is permitted to see results from any game.
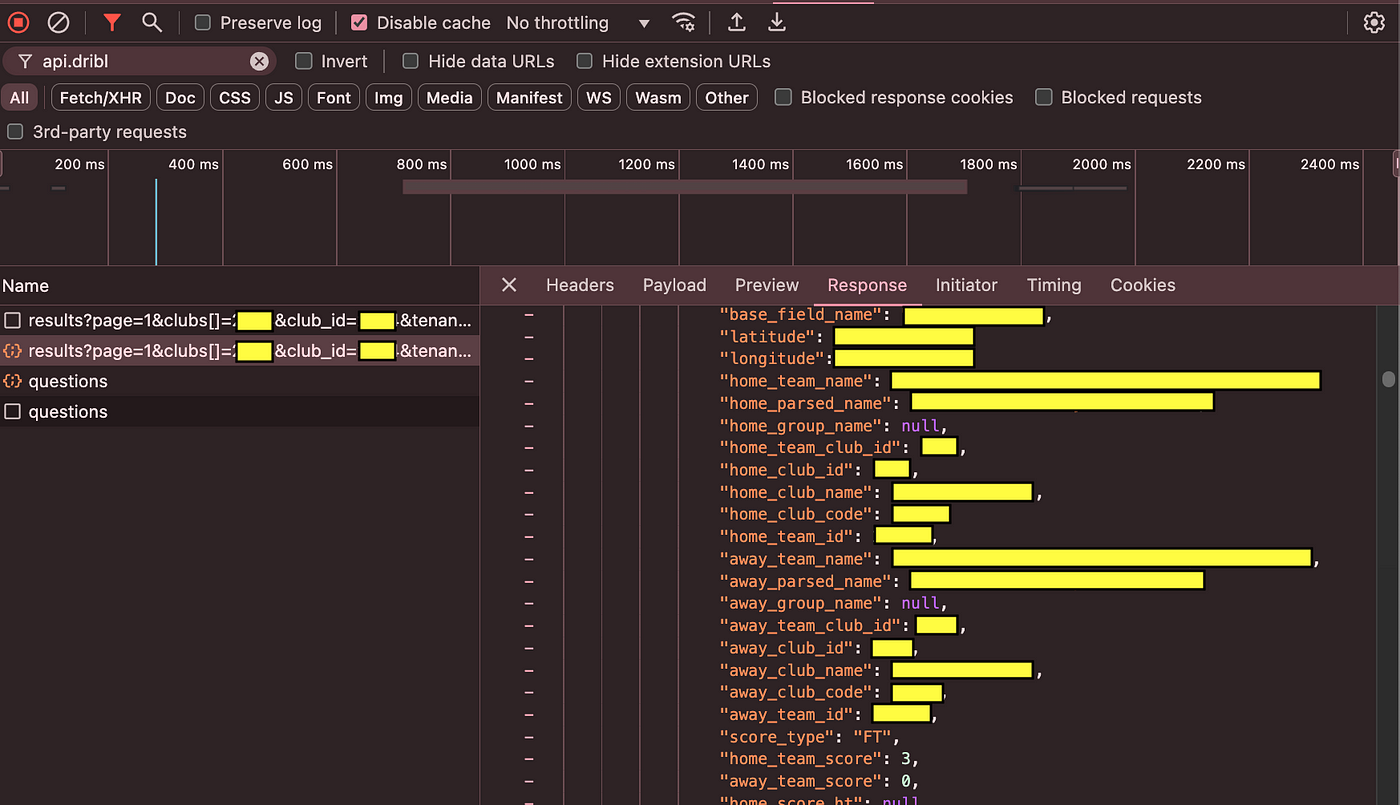
So we can hit the matchsheet-members endpoint to get info on the players of each match. This endpoint requires you to be signed up as a coach.
Hold on. Is that a phone number?
- First name, Middle name, last name: _Public info_
- Federation number: Limited to authorised users
- Personal email and mobile number: Not meant to have this.
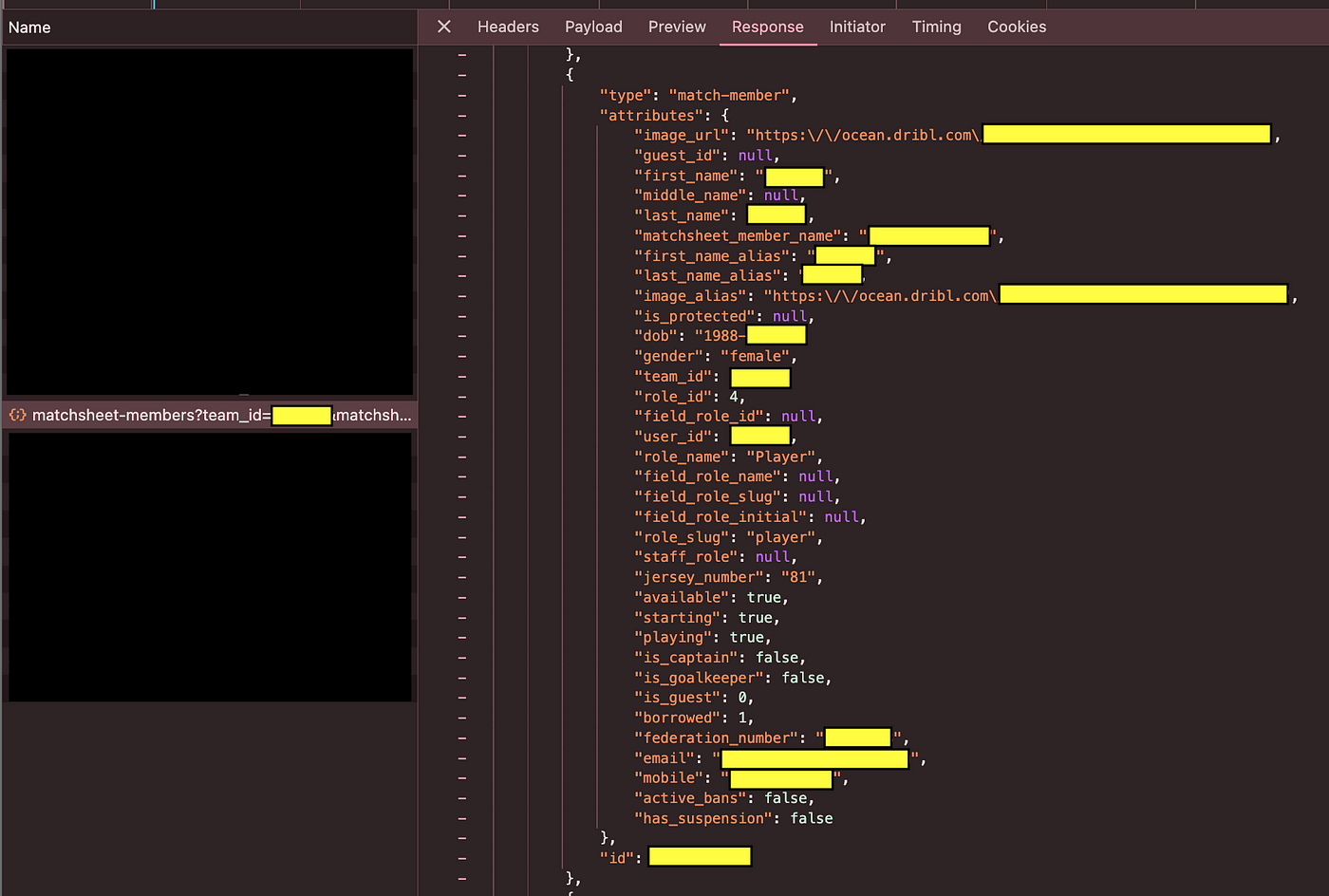
As a member of this league, I can see teamsheets for every team we've versed. This means the names, emails and phone numbers of every player in the league are being sent to anyone logged in and browsing a teamsheet...
Contacting the app.
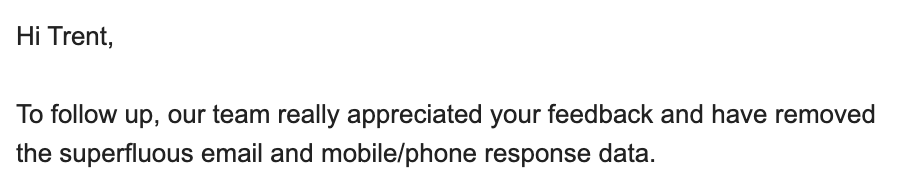
Nobody wants to be the next Optus. I contact the app, they respond within an hour or two saying it's been patched!

Finding something even worse.
I came back to this a week later, looking for stats on both the teams I coach and play in. From the coach admin portal, I can hit the /members endpoint to retrieve all members in MY club.
Have a look at the URL and take a guess what we'll tinker with next:
https://api.<Some App>.com/api/members
?page=1
&tenant_id= <id>
&season_id= <id>
&club_id= <id>
Trent! You exclaim. You couldn't possibly guess other tenant IDs/Club IDs!? Surely they are UUIDs.
Oh to have such faith.
All IDs in the system seem to be incremented numbers. Leaving entities open to an enumeration attack.
Hitting the /tenants endpoint with id = n (n= 1…1000) will retrieve the ID and name, which can be combined with another endpoint to retrieve contact information for all tenants.
This /members endpoint provides me with not only the phone number, and personal email from before, but also the profile picture, date of birth and home address of each user. Regardless of if I should have permission to them or not.
Change the club ID? Theoretically Get data for every single member assigned to that club.
There are over a million users on this platform, including minors.
According to UpGuard, a coordinated effort for this would land at the 5th largest (publicly known) breach in Australia.
Do I email the developers again, so they can fix it, and sweep this under the rug?
Or contact someone in a higher position in the digital world, with unknown consequence on either side?
In university, ethical questions like "would you delete accidentally-sent emails from a friend's account if your boss told you to?" were great talking points, but are detached from genuine circumstances.
On one side, I like this app. It saves me time and helps coordinate those million+ people to play the game they love.
On the other, I can't believe a company can reach millions of users and Australia-wide success without being scrutinised enough to have checked these endpoints.
Everything I've shown today can be done within a browser. In the first instance, sensitive data was being sent to clients while using the app as intended.
Telling them, and their response.
This is all new territory for me. I didn't know how anything could come back at me, so after a few conversations, decided to tell the app developers as soon as possible and get that data off the market.
I compiled everything into one email. Steps to recreate, required permissions, affected areas and my suggested changes, encouraging them to have a further look into their endpoints with sensitive data.
I didn't know what to expect as a response.
Something with an understanding of the gravity/severity of what I've just handed them would be nice. But I guess the last thing a company wants to do is admit that.
Either way, for now I can rest easier knowing my personal data is a tiny bit safer.
(*1): _I know you can go a lot further when inspecting packets from an app, but there's also a skill in recognising other avenues are of lower time cost._